Your Path to Secure Access in the Cloud Era
We've moved on from ethernet connections, dial up, phone lines. The traditional network perimeter has dissolved and cloud adoption is the norm, and now securing your data and applications is more complex than ever. This complexity often brings confusion, especially around hot topics like Secure Access Service Edge (SASE) and Zero Trust.
To cut through the noise and provide a realistic view, we've got the insights from Softsource vBridge CTO, David Small, on SASE and its practical application here in New Zealand.
Read on to get the key facts on what SASE is, why it's crucial to understand, its core components, and how to approach selecting the right solution for your business.
What is SASE Anyway?
Ultimately, SASE (pronounced 'sassy') is not entirely new technology but rather a framework or concept, first defined by Gartner around 2019. It bundles together existing technologies to address security and access challenges at the network edge.
It emerged as a response to the significant shift away from the traditional "castle and moat" security model focused on the data centre.
With users now working remotely, accessing cloud applications (like Microsoft 365, CRM, ERP systems) from various locations and devices, the old model of backhauling traffic via VPN to the corporate office firewall (tromboning) can be inefficient, slow, and misaligned with how people work and access data today. SASE aims to solve this by moving security closer to the user and the cloud services they access.
Breaking Down the SASE Stack
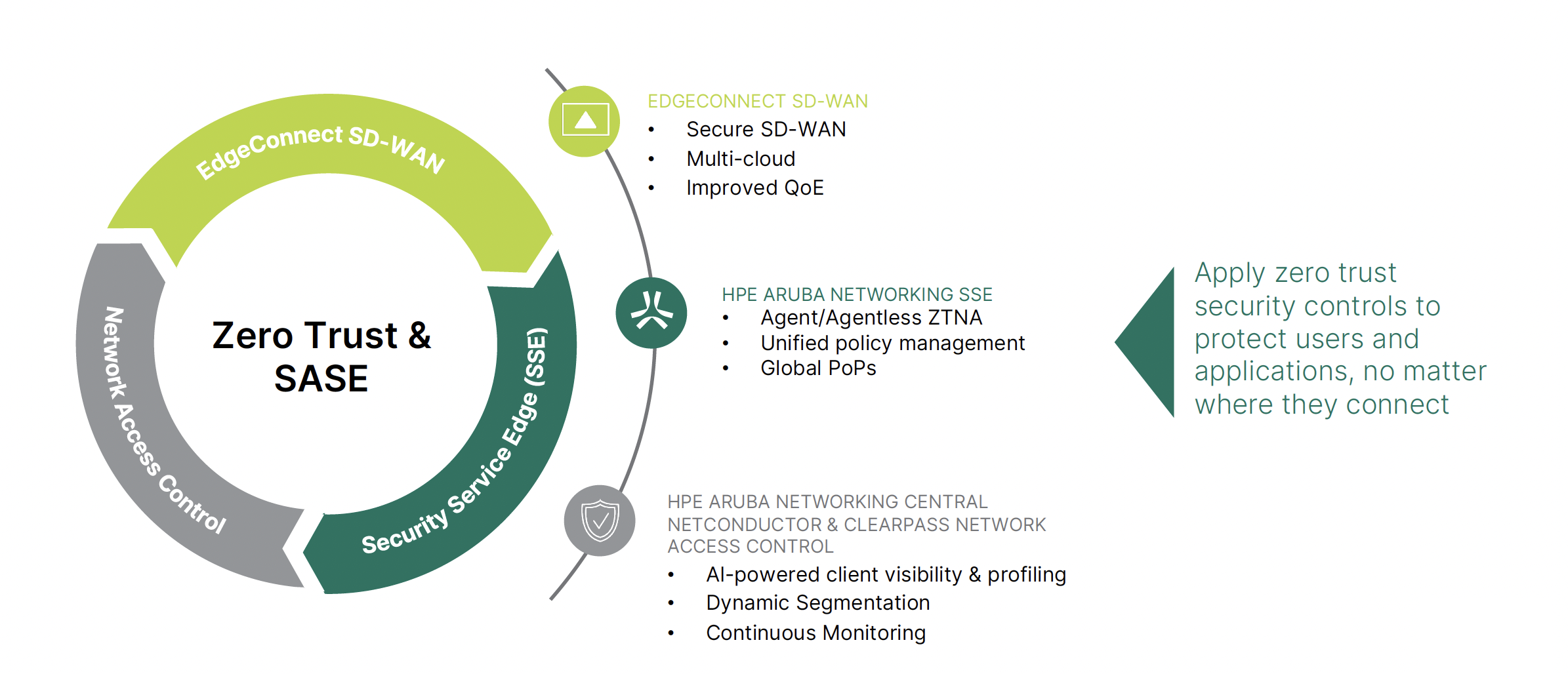
Our CTO David Small explains: a true SASE model is typically made up of four key components.
Secure Web Gateway (SWG)
Acts like a firewall in the cloud, protecting users from malicious web content and enforcing web access policies.
Cloud Access Security Broker (CASB)
Provides visibility and control over data and threats within cloud services. This has been around for about a decade.
Zero Trust Network Access (ZTNA)
Replaces traditional VPNs by providing secure, identity-aware access to specific applications, rather than the entire network.
Software-Defined Wide Area Network (SD-WAN)
A networking component that improves performance and reliability by intelligently routing traffic, allowing direct internet access for cloud traffic while routing internal traffic back to the corporate network.
It's important to note the distinction: SD-WAN is a component of SASE, not a replacement for it.
Because some security vendors lacked the SD-WAN piece, Gartner introduced another acronym around 2021: Secure Service Edge (SSE). SSE combines the security components – SWG, CASB, and ZTNA – making it a subset of the full SASE framework. Many vendors who claim "SASE" may actually only offer SSE.
Zero Trust, full protection
You're probably aware of Zero Trust by now: the overarching strategy or architecture, the principle that you "trust nothing" unless verified. It's a journey involving concepts like identity verification, microsegmentation, and strong policy management.
SASE, on the other hand, is a key implementation model that aligns perfectly with Zero Trust principles. While you can implement Zero Trust without a full SASE solution, SASE can't be implemented without Zero Trust (just as all thumbs are fingers, but not all fingers are thumbs).
SASE's integration of identity-aware security and granular access controls helps fulfil the Zero Trust mandate of verifying every user and device before granting access to resources.
Why Understanding SASE is Important
The shift to cloud and remote work isn't just a temporary trend; it's the modern way of working. SASE is crucial because it offers:
- Improved Performance by allowing direct, secure access to cloud apps, eliminating the latency caused by tromboning traffic back to a central data centre.
- Enhanced Security Posture through consistent, identity-driven security policies regardless of where the user is located or what device they are using.
- Simplified Management via a single SASE platform that manages multiple security and network functions, reducing complexity compared to managing disparate point solutions.
- A flexible and secure foundation needed to support cloud adoption, remote work, and edge computing initiatives.

Selecting the Right Solution
Look for a Full Stack Provider
While you may not need all components immediately (especially SD-WAN), choosing a vendor that offers the full SASE stack allows for future integration and simplified management down the line. Don't be fooled by vendors claiming SASE when they only offer SSE. Drill down and understand their capabilities.
Trying to stitch together SWG, CASB, ZTNA, and SD-WAN from different vendors can lead to integration headaches and complexity, undermining the SASE promise of simplified management.
Prioritise Based on Risk and Reward
As an IT manager, assess where your greatest security risks are and where you can achieve the biggest reward for your efforts.
David recommends starting your Zero Trust/SASE journey by strengthening identity management, leveraging existing tools like Azure AD/Entra ID if possible. Establishing a strong, single identity for users and devices is foundational.
Integrate Strategically
If you have a pressing need for a WAN upgrade or network transformation, integrate SD-WAN into your decision, but ensure the chosen vendor fits into your broader SASE vision.
For many businesses, the easiest and fastest way to gain value is by implementing the SSE components (SWG, CASB, ZTNA) first. These are often software-driven, require no physical assets, and can quickly address issues with VPN performance and cloud application security. This can often solve immediate problems related to roaming users and cloud access.
Considering services like Network as a Service (NaaS), like the offering Softsource vBridge has partnered with HP Aruba on, can also fit into this strategy, particularly for businesses favouring an OpEx model for network infrastructure (wireless, wired, WAN), aligning the delivery model with cloud-based SASE security.
The steps for a safer future
To effectively leverage SASE and build a robust security posture:
- Assess Your Current Infrastructure
Understand your existing environment to identify gaps and plan your transition.
- Choose a Comprehensive SASE Provider
Don't just look for a single component; find a partner who can support your journey towards a full SASE model.
- Implement Gradually
Tackle the most critical areas first (often identity and SSE) and expand your implementation over time.
- Train Your Team
Ensure your IT staff understand the new architecture and tools.
- Monitor and Optimise
Security is ongoing. Continuously review and refine your SASE implementation to adapt to new threats and business needs.
David advises that regarding resistance to things like Privileged Access Management (a Zero Trust component), while some "old hats" may resist giving up broad permissions, younger developers often pick it up faster because they've been trained with security in mind.
Implementing these layers is about building a more secure environment, even if it adds a small step (like privilege elevation) to a task.
It's a necessary habit change for better security hygiene.
You don't need to do it alone.
Navigating the complexities of SASE and Zero Trust requires expertise. Softsource vBridge is here to help you understand your options and develop a strategy that aligns with your specific business needs and goals. Whether you're driven by infrastructure upgrades or the need to secure cloud and remote access, we can guide you through the process.
David advises that it's about understanding what you want to achieve and finding a vendor or partner who can help you build that full picture over time. We can discuss your environment, identify your greatest risks and potential rewards, and help you take the right first steps, whether that's focusing on identity, SSE built for future growth, or an immediate SASE rollout.
Contact Softsource vBridge today to discuss your security path forward and how SASE can benefit your organisation.
The future belongs to those
who prepare for it today
- Martin Luther King